What Is Sign & Encryption?
Digital communications security depends on the cryptographic techniques of Sign & Encryption as essential components. Digital signatures originate from private keys that enable users to verify message or document authenticity together with integrity while confirming that no alterations occurred. A non-repudiation service is built into this signature process, making it impossible for senders to dispute that they authorised the signing. Through encryption techniques, data becomes unreadable ciphertext because of algorithms such as AES or RSA, and only authorized recipients with proper decryption keys can retrieve the original information.
The security function of signing helps to prove identities and prevent tampering, whereas encryption keeps data confidential because it keeps unauthorised users away from accessed information. The combined mechanism of signing and encryption creates an extensive secure system that authenticates both the source and content and also maintains data secrecy. The widespread adoption of these techniques powers secure email systems (PGP) while securing online transactions (SSL/TLS) and enabling legitimate e-signatures, which are fundamentally necessary for cybersecurity and compliance needs of digital operation.
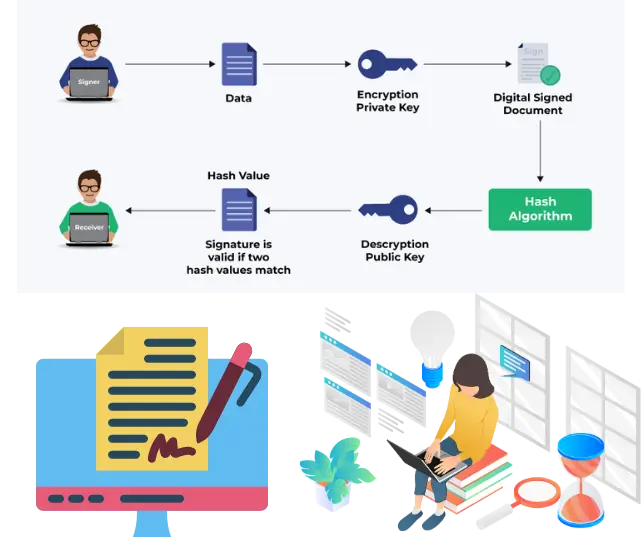
Why Sign & Encryption Are Essential?
Data Security First
The system uses strong cryptographic methods to deliver total protection against hacking attempts as well as data leaks, which defends sensitive information from unauthorized
access.
Secure Transactions
Digital exchanges are protected from modification and acquisition attempts through this security mechanism, which guards financial operations together with sensitive communications and contracts.
Prevent Data Tampering
Digital signatures alert users to all unsanctioned modifications done to documents or messages to guarantee the information stays
unchanged since its original
creation.
Verify Authenticity
Digital signatures authenticate senders as well as sources to recognise thousands of potential sender identities, including businesses and individuals.
Confidentiality Guaranteed
Safeguarded communication, along with file storage, depends on encryption because the process protects sensitive information from anyone other than official recipients.
Trust in Digital
Electronic systems gain credibility from users because security verification protects
both online services and digital
documentation.
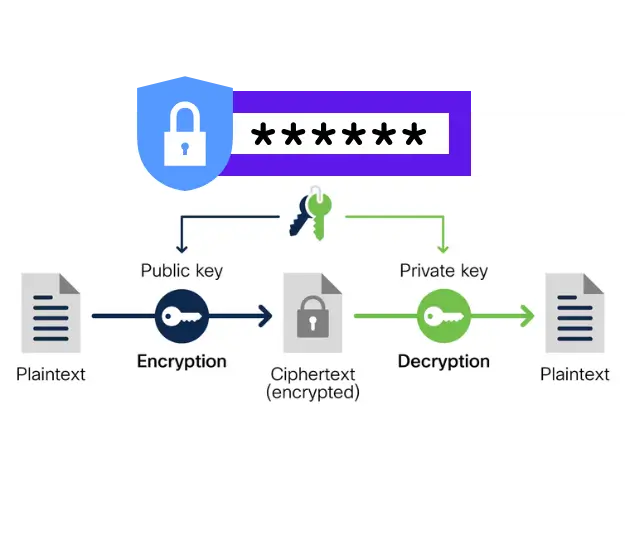
The Need for Encryption
Digital communication confidentiality depends on encryption because it protects valuable data points from unauthorized intrusion. Encryption processes information into unrecognizable ciphertext while authorized parties need valid keys to decrypt it. Hackers who did not use encryption would gain access to sensitive personal data plus financial transactions, as confidential business communications resulting in data breaches and identity theft and financial fraud. Various industries like banking and healthcare under the HIPAA requirement together with e-commerce under PCI DSS depend on encryption for regulatory compliance and protecting user privacy.
The Need for Signing
The process of signing creates data integrity and authenticity that proves the message originates from an authenticated source without changes. Modern signatures implement cryptographic methods that establish a connection between data and user identity while stopping unauthorized changes to content. Non-repudiation (proof of origin) becomes essential in legal contracts and software updates as well as secure transactions. The signing process enables governments, through their respective legislations (eIDAS and ESIGN Act), along with enterprises, to validate agreements while fighting fraud and creating auditable trails.

Sign & Encryption: How They Work Together
| Feature | Signing | Encryption |
|---|---|---|
| Purpose | Verify authenticity & integrity | Protect data confidentiality |
| Key Used | Private key (sign), Public key (verify) | Public key (encrypt), Private key (decrypt) |
| Output | Digital signature | Encrypted ciphertext |
